Verifying users are who they say they are
Two-factor authentication (2FA) – the need of two methods of authentication factors to verify user’s identity. 2FA aims to strengthen user’s access security, preventing attackers from exploiting weak login credentials with the introduction of an additional authentication factor. These factors can include:
- Something you know – e.g. password, PINs
- Something you have – e.g. smartphone, OTP token
- Something you are – e.g. fingerprint, biometrics
How 2FA works?
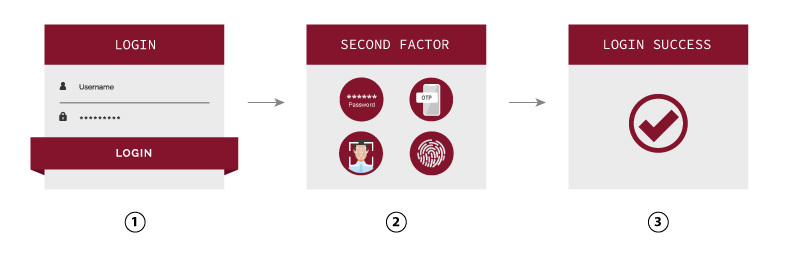
i-Sprint Two-Factor Authentication Solution

Seamless Integration
The pre-integrated and tested solution allows the i-Sprint 2FA solution to be deployed rapidly across applications and systems. Moreover, the solution supports various brands of OTP tokens and common applications.

Full Life Cycle Token Management & Administration
Integrated solution for administering the entire life cycle of token management functions: issuance (factory initialized or self initialized), delivery, enablement, lost tokens, out-of-sync, and replacement over time.

Ensure Compliance and Provide Detail Audit Trail Information
Provides user administration, authentication, authorization and audit services (4As) to address security and compliance requirements.

Multiple Authentication and Transaction Authorization Options
Includes: synchronous option with one-time password challenge, an asynchronous option with challenge and response codes, the re-authentication challenge for critical transactions and inclusion of additional static password.
*i-Sprint 2FA solution allows integration with SingPass/ CorpPass (SPCP) using SAML 2.0 protocol. It also supports Assurity OneKey Token using the Singapore Technical Reference TR-29 protocol.
