- IAM Products
- Identity and Access Management (IAM)
- IAM as a Service
- Mobile Security
- Product Authentication
- Solutions
- IAM
- MAS TRM
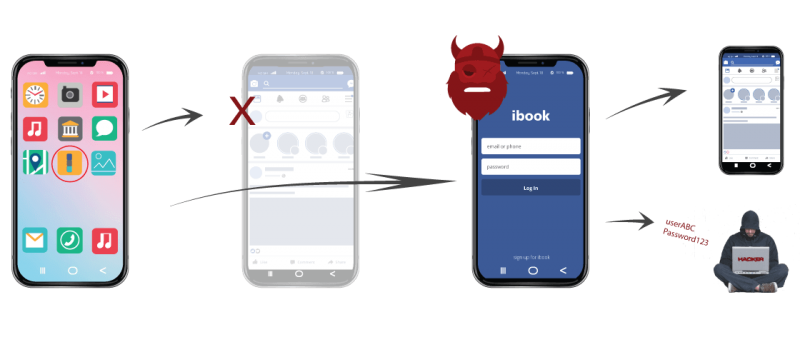
- AppProtect+ for StrandHogg
- Enterprise Access Control
- Enterprise Single Sign-On
- SSO with Portal Integration
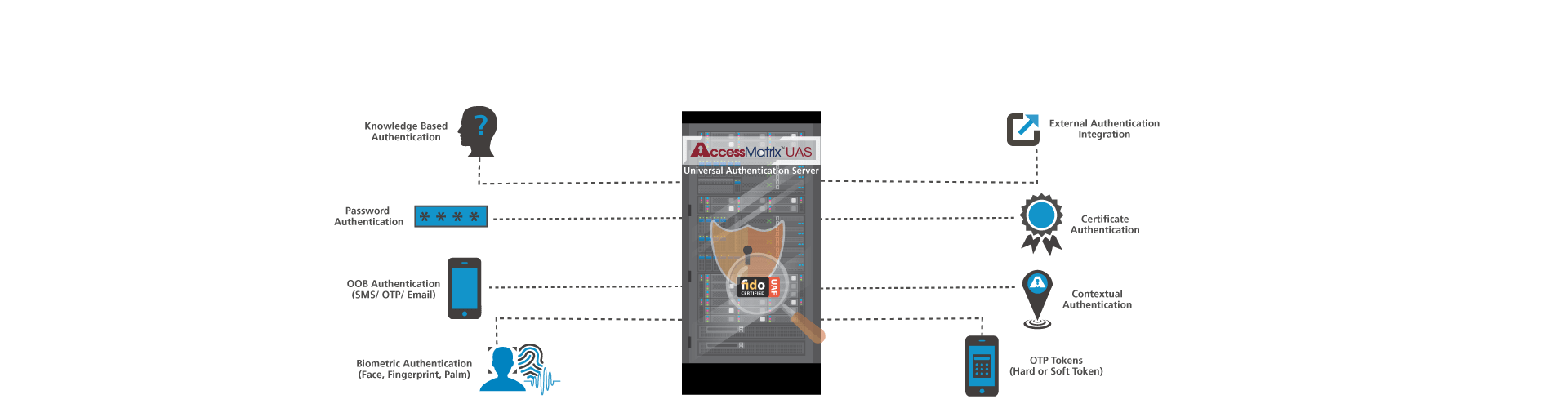
- Future Proof Authentication
- End-to-End Encryption Authentication (E2EEA)
- Enterprise Two Factor Authentication (E2FA)
- 2FA Solution for Banking
- 2FA: Strengthening User Access Control
- Multi-Factor Authentication (MFA)
- Securing Online Trading Platform
- Biometrics Authentication Platform Solution
- Brand Protection
- IAM
- Resources
- Partners
- Customers
- Newsroom
- Company
- Support